| frontend | ||
| greenhouse-daemon | ||
| pki | ||
| readme | ||
| schema_versions | ||
| threshold | ||
| .dockerignore | ||
| .gitignore | ||
| backblaze_b2_service.go | ||
| backend.go | ||
| build-docker.sh | ||
| db_model.go | ||
| digitalocean_service.go | ||
| Dockerfile | ||
| easypki_db_adapter.go | ||
| email_service.go | ||
| example_config.json | ||
| frontend.go | ||
| frontend_admin_panel.go | ||
| frontend_howto.go | ||
| frontend_login.go | ||
| frontend_profile.go | ||
| gandi_service.go | ||
| go.mod | ||
| go.sum | ||
| ingress_service.go | ||
| LICENSE.md | ||
| main.go | ||
| public_api.go | ||
| README.md | ||
| scheduled_tasks.go | ||
| ssh_service.go | ||
| telemetry.go | ||
| threshold_provisioning_service.go | ||
🌱🏠 greenhouse
Instant port-forwarding with automatic HTTPS, for everyone everywhere!
Greenhouse is sorta like CloudFlare's popular tunnel product, but completely redesigned to follow the Principle of Least Authority; to put the TLS encryption keys and ownership/control back into the self-hoster's hands.
At your command, Greenhouse can give any local file or service a secure URL in seconds. Send this URL to anyone or anything; as long as your computer is still running and has internet access, it should stay online.
Command-Line Interface
Graphical User Interface
Check it out at:
greenhouse.server.garden
⚠️ Please Note ⚠️ This is "alpha" software, it's currently not the most stable thing in the world.
what makes greenhouse different
You run the open source Greenhouse self-hosting software on your computer. This software has an instance of Caddy embedded inside it, and that Caddy server automatically issues a TLS certificate for you through Let's Encrypt. (TLS stands for Transport Layer Security, sometimes also known as its older name "SSL").
The TLS private key associated with your certificate is created on your machine, and it never leaves your machine. That means you "own" the traffic going in and out of your machine not just on paper, but in real terms, you have complete physical custody of it and you would be able to audit or modify any part of it if you wanted.
This is not the case with a traditional cloud service like DigitalOcean or CloudFlare. With those services, the service provider is the one who holds physical custody of the server and/or its data / encryption keys. They can theoretically spy on you or your website visitors as much as they want.
project goals
Greenhouse aims to make self-hosting ✨radically easier✨ for the average person. No matter who you are or where you live, as long as you have an internet connection, you can run your own reliable web site or web service with Greenhouse!
In the future, Greenhouse will be easy to use with existing self-hosting solutions like yunohost, syncloud, and others.
For more information about the motivation behind greenhouse, see my blog post about it: The "Pragmatic Path" 4-Year Update: Introducing Greenhouse!
FAQs
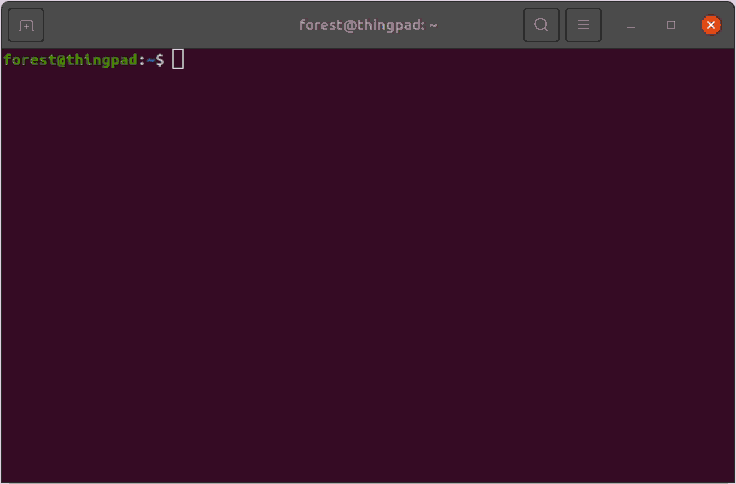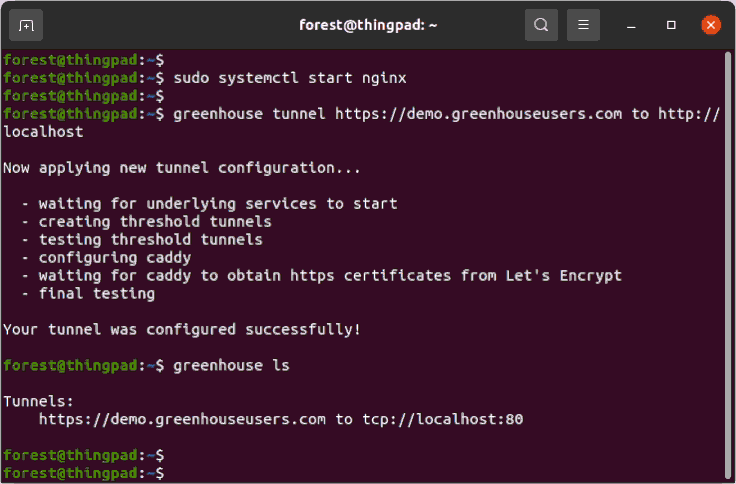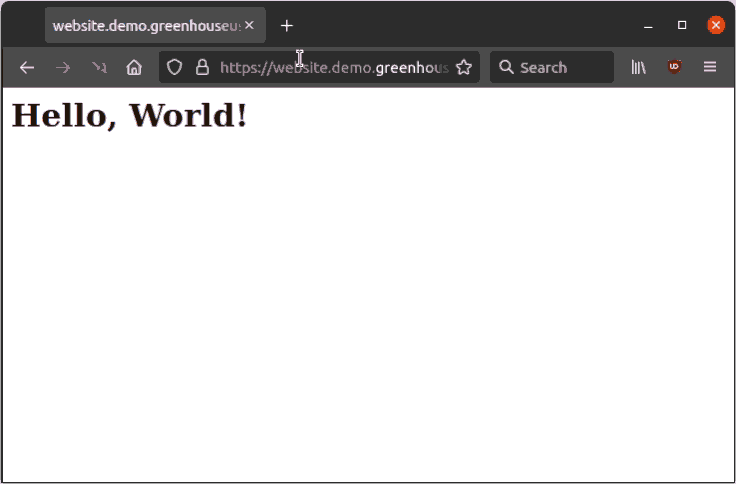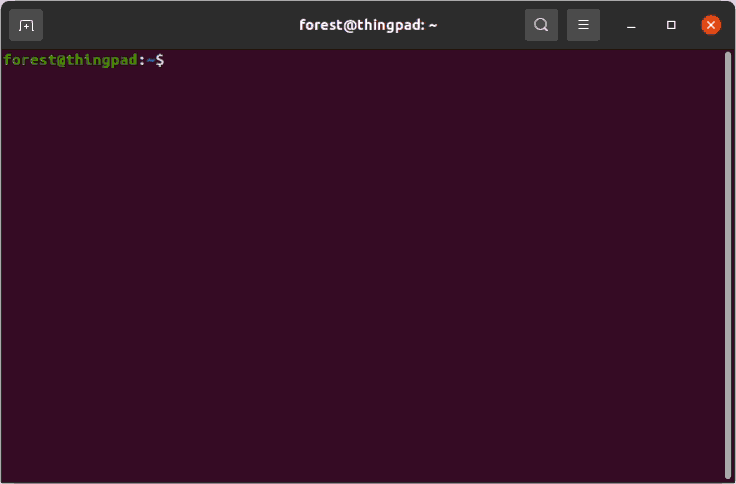
how does it expose my server on the internet so other people can connect?
It creates a TCP reverse tunnel to a 🏔️🛤️🏔️ threshold server running on a Virtual Private Server (VPS) located in a public cloud. (Right now it's running the threshold server on a DigitalOcean droplet)
what the heck is a "TCP reverse tunnel"? Is that like a VPN? 🤨
I made an infographic to explain the terminology.
Yes, it is sort of like a VPN designed for routing incoming connections from the internet.
However, unlike a VPN, it doesn't require root access to your computer, it doesn't create virtual network devices or change your routing rules, and it only exposes one port on one computer at a time by design. See my introductory blog post for more details.
why not just configure port forwarding on the router instead?
Because not everyone can log into thier router to do that. For example, people who live in a dorm, share wifi from thier nieghbor, get internet exclusively via LTE/5G, or run linux inside an older version of chromeos.
We think it's important that everyone gets a chance to fully participate (own & operate a server) on the internet, no matter who or where they are.
Also, it's just easier. The port forwarding guide at portforward.com is quite long and covers networking concepts that many people, even deeply technical people, aren't familiar with. Compare that with the straightforward setup process shown in our alpha release demo video.
but why a "cloud service"? doesn't that defeat the purpose of self-hosting?
For the same reason most self-hosters don't operate thier own ISP (Internet Service Provider): It's too difficult, expensive, and time consuming!
If you don't depend on a service to manage/maintain the network, that means YOU have to manage/maintain the network. For some people that's tiresome, and for others it may even be impossible.
In many ways, Greenhouse is less like a cloud service and more like a specialized micro-ISP. We piggy-back on your existing internet connection in order to make your computer dial-able on the public internet. Greenhouse specializes in providing the features self-hosters want, features which most residential ISPs don't give rat's ass about:
- Static IP / Dynamic DNS
- Greenhouse is designed to eliminate DNS caching issues from your life 😌
- Reverse DNS Records (planned for beta version)
- Support Hosting Email Servers (planned for beta version)
- Built in Redundancy/Failover (planned for later)
Often the residential ISP will even prohibit certain types of self-hosting, for example, if you want to run an email server at home, there's a 99% chance you'll end up having to depend a public cloud anyways: Your internet service provider will not allow you to do the things you need to do in order to run an email server.
is this safe? someone told me that opening up my home network to the outside world is dangerous!! 😱
First of all, yes, there are risks associated with self-hosting. There are also risks associated with browsing the web or riding in a car.
You should be informed, but at least in our opinion, you shouldn't be afraid of self-hosting.
Greenhouse only exposes exactly what you tell it to, and by default it exposes nothing. For more information, see SECURITY.md.
related repositories
This git.sequentialread.com/forest/greenhouse repository only houses the web application for the cloud service. There are many other applications and processes involved in making
greenhouse work, and making it easy for anyone to use. They are all open source!
-
🏔️🛤️🏔️ threshold
- Public Internet facing gateway (TCP reverse tunnel) server/client that greenhouse uses
-
🔒 caddy
- A slightly modified fork of the Caddy 2 HTTP server by Matthew Holt / Let's Encrypt
-
🌱🏠😈 greenhouse-daemon
- The core of the greenhouse self-hosting software that you run on your server computer
- Embedded threshold client makes your server avaliable on the internet through the Greenhouse threshold server(s)
- Embedded Caddy Server (optional)
- Handles TLS (HTTPS) encryption keys and certificates for you automatically and securely
- It can also serve your files on the internet for you
- The core of the greenhouse self-hosting software that you run on your server computer
-
🌱🏠🖥️ greenhouse-desktop
- Cross-platform desktop application for greenhouse -- an interface to the greenhouse daemon. Share your local servers or files on the internet in seconds!
-
🌱🏠🧑💻 greenhouse-cli
- command line interface to the greenhouse daemon
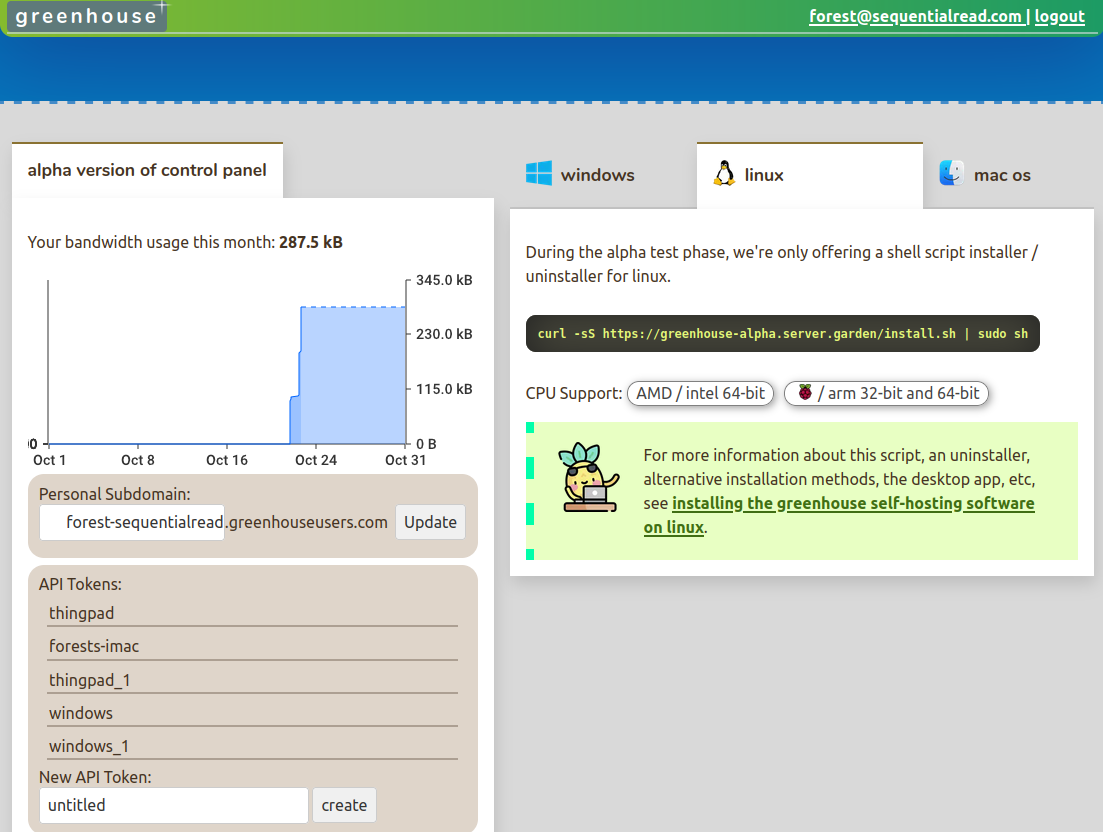
screenshot
alpha release demo video
See https://sequentialread.com/greenhouse-alpha/
Dev Notes
TODO: everything here is moderately to severely outdated.
setup local environment
Write the config file config.json in the root directory:
{
"FrontendPort": 8080,
"FrontendDomain": "localhost",
"DatabaseConnectionString": "host=/var/run/postgresql port=5432 user=postgres password=dev database=postgres",
"DatabaseType": "postgres",
"DatabaseSchema": "public",
"SMTP": {
"Host": "<my email server>",
"Port": <587 (SMTP+STARTTLS) or 465 (SMTPS)>,
"Username": "<my email address>",
"Password": "<my email password>",
"Encryption": "<SMTPS or STARTTLS>"
}
}
Run the database:
mkdir -p postgres-data
docker run --rm -it -e POSTGRES_PASSWORD=dev -v /var/run/postgresql:/var/run/postgresql -v "$PWD/postgres-data":/var/lib/postgresql/data postgres
Run the app:
go run *.go
Inspect the database:
sudo apt-get install postgresql-client
PGPASSWORD=dev psql --host /var/run/postgresql --port 5432 --username postgres -d postgres -c 'select * from session_cookies'
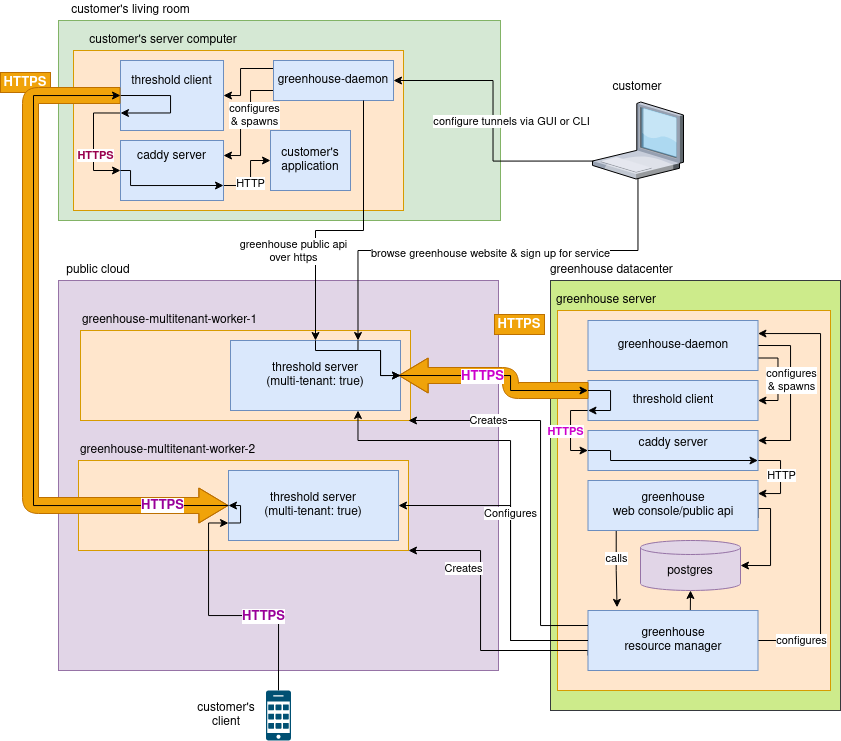
architechture
This diagram was created with https://app.diagrams.net/. To edit it, download the diagram file and edit it with the https://app.diagrams.net/ web application, or you may run the application from source if you wish.
Features:
- Threshold (TCP reverse tunnel) as a service (multi-tenant or dedicated IP address)
- Object Storage
- free subdomains (like duckdns / freedns.afraid.org)
- managed domain names (like njalla)